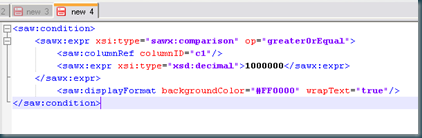
The ATR files in the OBIEE repository manage privileges on a item and provide a “readable” text for both the name and description of an object. Dan Malone of Calpoly did some basic research on how these work.
This article describe the build up of the ATR file when used for a report.
WOW: backup the files before you start to hack them, one misplaced byte can really f*&^k up your system!
Let’s get out our trusty “hexplorer” and open an ATR file:
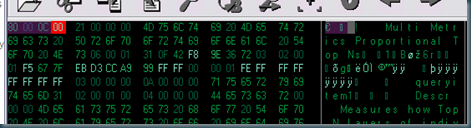
Bytes 00.03 {4} => File Standard; Seems to be always the same

Byte 04 {1} => Length of the object name; Name starts 4 bytes from here.
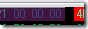
Byte x..03 {3} => Prequel to object name

Byte x..Byte 04 {Byte 04} => Object name as ascii.

Byte x..11 {11} => prequel 06 00 01 + Hex id of the object owner

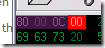
Byte x {1} number of users / groups which have form of permission.

Byte x..13 {13} => Prequel 00 01 {2} + Hex id of the grantee (group or user) {8} +
permission: (FF FF 00- Full Control ; 0F 00 00 - Change/Modify ;03 00 00 – Read; ◊02 00 00 – Traverse ; 00 00 00- No Access ) {3} [for each grantee]

Byte x{1} length of the object type name:
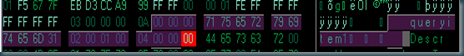
Byte x .. 3+byte(x-1)+8 => Prequel 00 00 00 {3} + Object type name as ascii + Sequel 02 00 01 00 04 00 00 00 {8}

Byte x..x+3{4} text Desc

Byte x{1} Length of description

Byte x..byte(x-1)+4=> prequel 00 00 00 {3} description in Ascii; sequel 00 00 00 00 {4}
Now in what way is this info useful? If you want to script your reports, you also need to script the ATR file.. I will hopefully soon have time to show you how to script a report.
Till Next Time